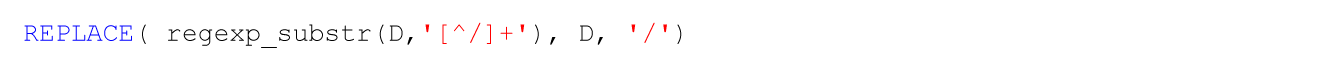APEX Blog
Latest Posts
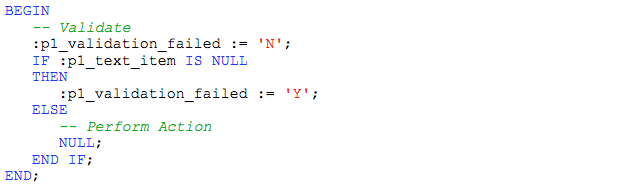
Combining Validations with Dynamic Actions
APEX has an extensive set of built-in validations to capture every eventuality. They pop up an informative notification message and can direct the user directly to the fault.
Creating a Mobile App in Apex 5.0
Since the release of APEX 5.0 EA3 I’ve been looking into the updated mobile theme and what we can produce with it. In this blog I will show you how I created a small demo..
Parsing JSON in APEX 5.0
As part of the APEX 5.0 Beta documentation there is a new APEX_JSON package available. This is a welcome addition that helps us integrate our applications with web services that..
APEX 5 zip file support
In this blog we’ll explore support for ZIP files within APEX 5 which listed as one of the “Additional Features” on Oracle’s newly released APEX 5 Early Adopter 3 edition.
Template Options of the APEX 5.0 EA3 Universal Theme
In this article we will explore Template Options which is a feature of the new Universal Theme first seen in APEX 5.0 Early Adopter 3.
In house vs outsource
So, you’ve decided to develop your own application. …but should you develop in-house, or outsource it? Maybe the answer could be ‘both’ You’ve been asked to commission a new..
BI for small businesses: be clued-up or get slowed-down
Business Intelligence is vital for growing businesses.
Your Business is Special: So why buy business software, designed for everyone else?
As a rule, the majority of businesses buy their business software ‘off-the-shelf’, but is the ‘one-size-fits-all’ approach really the best strategy?
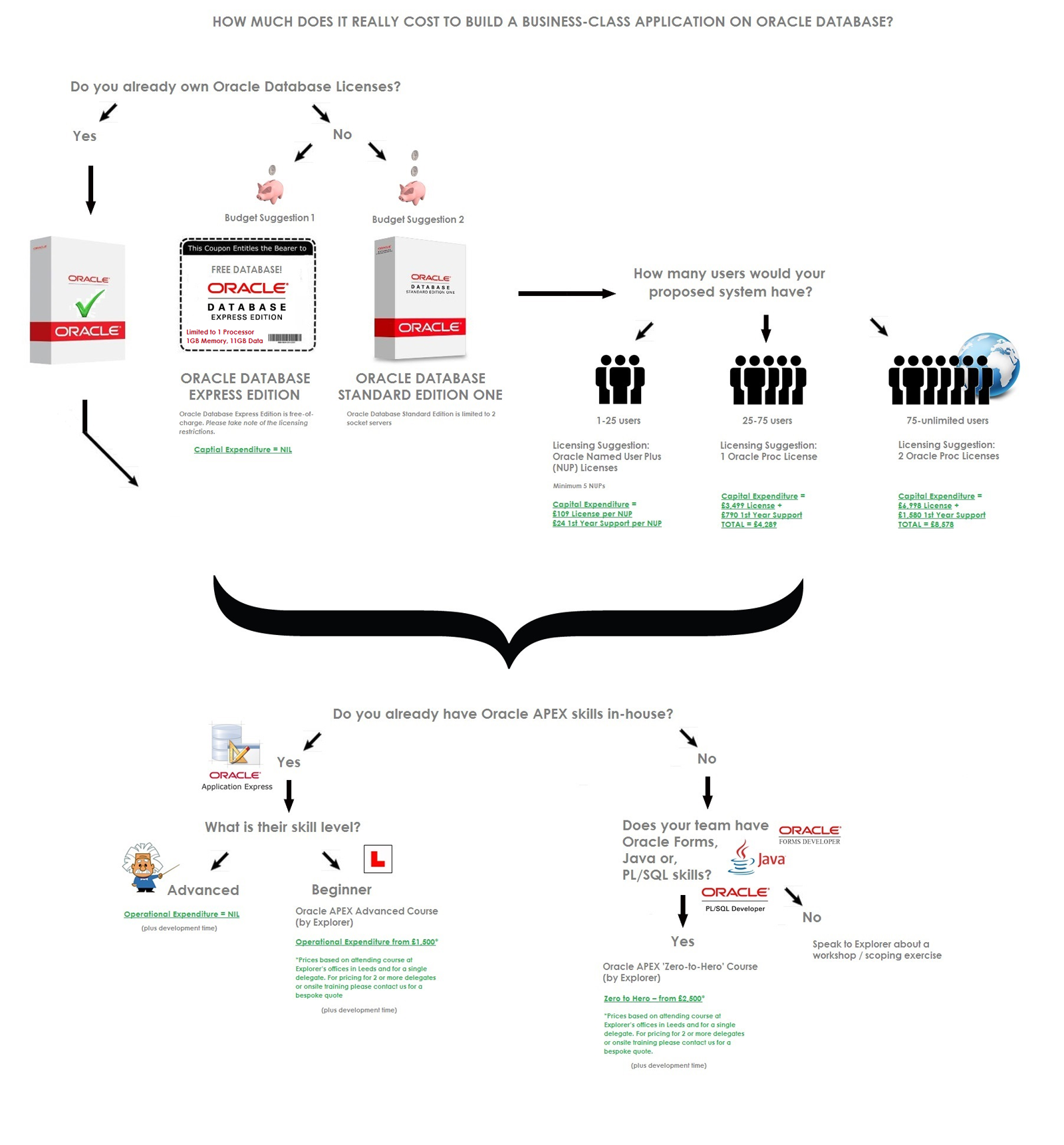
How much does it really cost to build a business-class application on an oracle database?
Answer: Surprisingly little with Oracle Application Express (APEX)
Popular Post

.png?width=250&name=stonewater-logo%20(1).png)