- About
Getting to know us
- Services
- Managed Services
- Application Services
- Cloud Services
- Data Science
- Consulting Services
- Technology Solutions
Managed Services
Application Services
Data Science
Consulting Services
Technology Solutions
- Industries
- Resources
Resources
- Contact
- Contact us
Maintaining Control and Consistency of Enterprise IT with Azure Arc
Contents
Azure Arc

In March this year Azure released Azure Arc for Public preview, following an announcement from Ignite in December 2019. Azure Arc is a way to extend the management of Virtual Machines and K8 services which reside in other Clouds or infrastructure into Azure. There are three main use cases; organise and govern, K8 app management, and deploy and manage resources anywhere.
VM Sprawl in the world of Public Cloud
For me the area that resonates strongest is organise and govern, simply due to the explosion of Cloud infrastructures. Several years ago I undertook a security project for a global retailer looking at their highly virtualised estate. Trying to measure and manage compliance was a challenge but achievable; what was interesting to me was how VM sprawl had outpaced the management information of these virtual machines.
Back in the day we had a physical server; you could touch it, see the lights flash and know there was a single OS to manage. Then virtualisation came along and suddenly one physical server became 20 virtual machines. Shortly after that we had multiple virtualisation platforms and vendors, and with the drop in costs of physical infrastructure multiple physical servers became virtual machine farms.
As this explosion happened there wasn’t really any tooling to help govern it. The tooling did catch up, but guess what – virtual machine explosion was turbo charged by Public Cloud. This meant physical infrastructure was and is no longer a constraint to the number of VMs you could have. With that in mind, the need for governance and control couldn’t be more relevant now.
Utilising Azure Arc
Azure Arc provides the ability to bring virtual machines into a single pane of glass in terms of management and governance. I have enabled it for my subscription of Azure resources and also added in an additional VM, which is running in another Public Cloud. As you can see dsp-msa-sql-vm1 is under a resource type of ‘microsoft.hybridcompute/machines’.
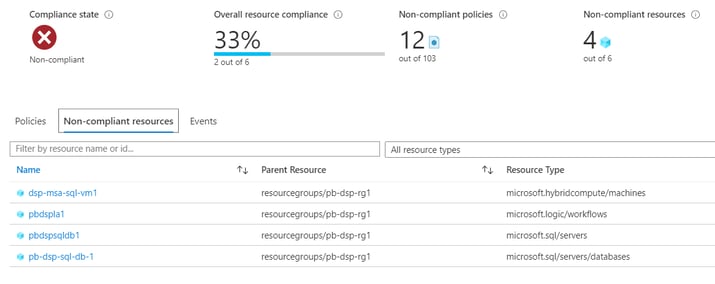
One of the things l really like is the ability to see your estate’s compliance position at a birds-eye view, but then drill into the specifics. Using the link above we can go into the next level of detail:
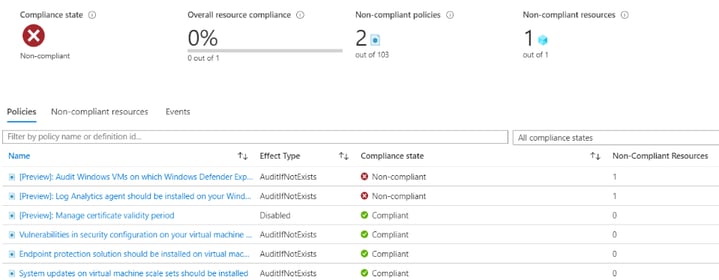
Being able to drill into the specifics of non-compliance provides the level of granularity needed. From here we can undertake remediation actions to resolve this non-compliance. It’s worth noting that both these elements of non-compliance relate to additional paid for services, i.e. Windows Defender ATP (Advanced Threat Detection) and also Log Analytics.
Therefore if you don’t run these services due to the additional costs, you may want to remove them from your compliance score. Your compliance policies in Azure should match your business outside of Azure; there is no point being complaint against policies which have no relation to your business requirements.
If you would like to learn more about Azure Arc and obtain assistance with a deployment please contact DSP at enquiries@dsp.co.uk or contact us at the numbers below. Alternatively, head to https://www.dsp.co.uk/microsoft-azure-csp to learn more about how DSP-Explorer work with Azure.

.png?width=250&name=stonewater-logo%20(1).png)
